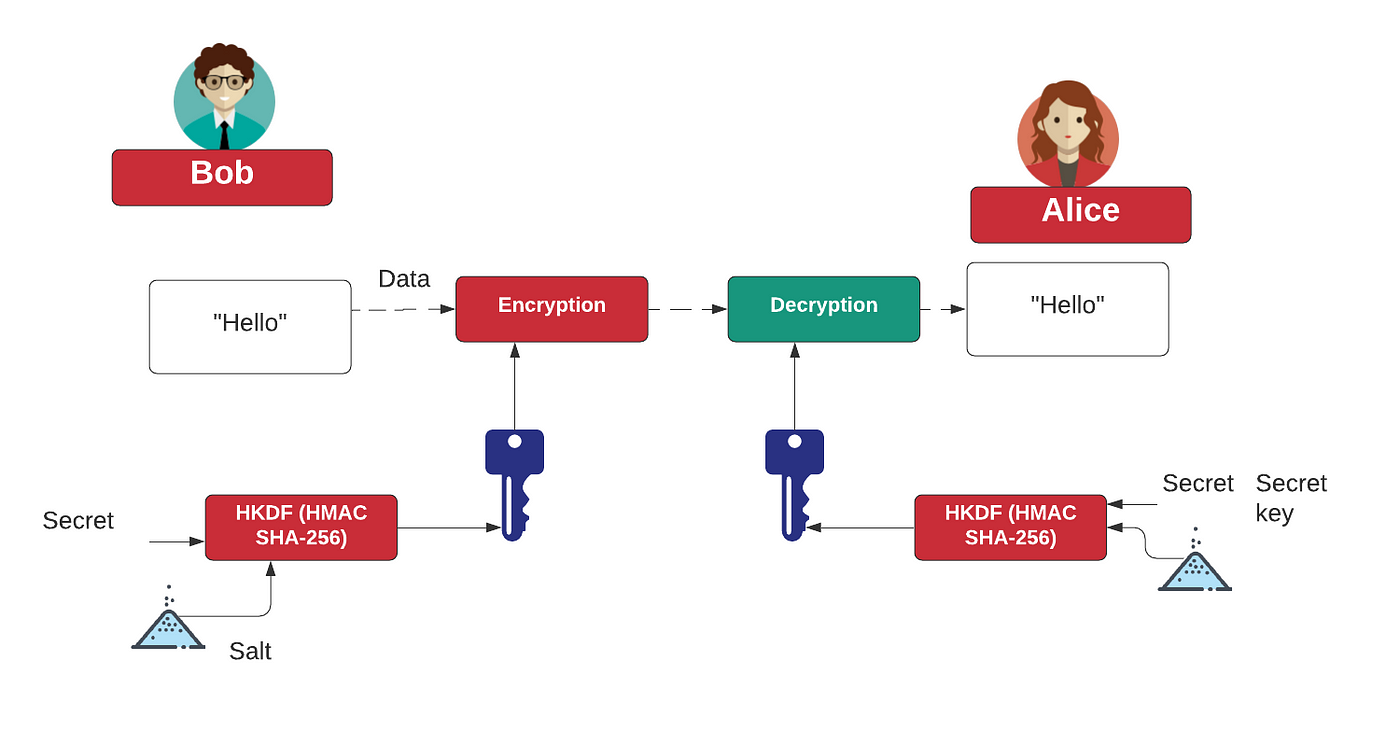
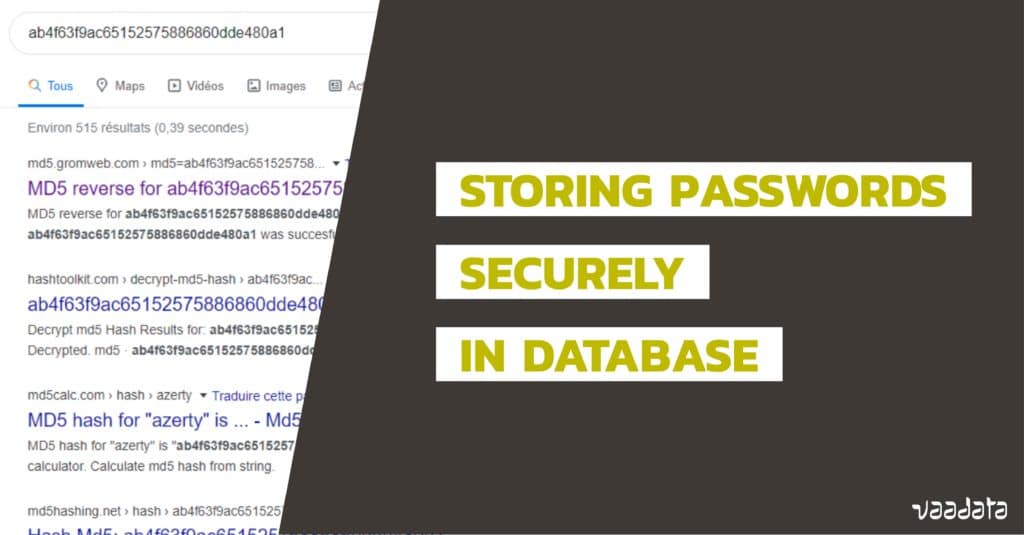
To Salt or Not To Salt? — Salting is not the only answer to securing passwords | by Prof Bill Buchanan OBE | Coinmonks | Medium

KALI – How to crack passwords using Hashcat – The Visual Guide | University of South Wales: Cyber University of the year: Three years running: 2019, 2020, 2021